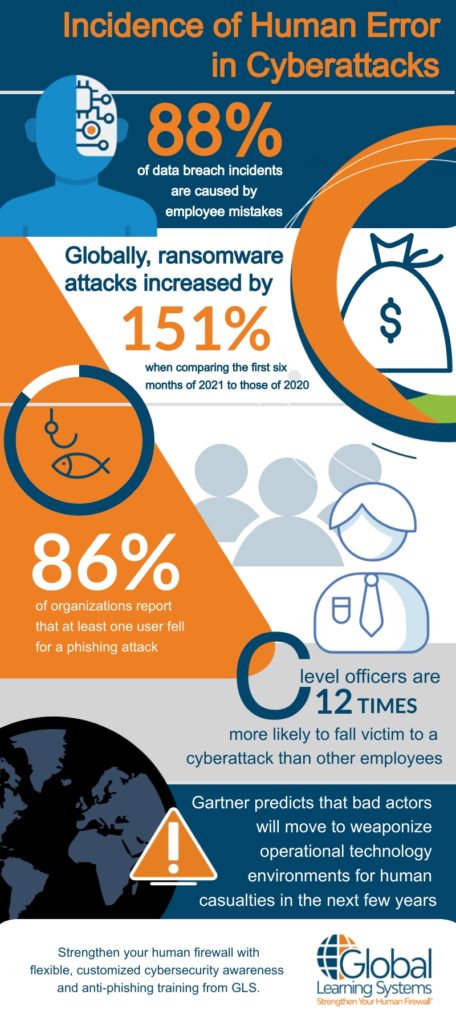
Almost daily, a cybersecurity event makes national or world news, highlighting the importance of training employees to acknowledge the role of human error in cybersecurity. An IT department can build a fortress of secure networks, hardware, and software, but a tiny crack in that framework can cause widespread attacks on your data and networks, often due to human error. Recent studies show that 88% of data breach incidents are caused by employee mistakes.¹
Cybersecurity awareness is such an essential component in keeping organizations secure, yet security awareness training is something that many fail to prioritize. Even organizations that implement security awareness training sometimes don’t get the desired results because the training is not engaging or memorable.
Increasing risk of cyberattacks
Phishing, ransomware and social engineering attacks are on the rise worldwide. Globally, phishing attacks increased by 151% in the first six months of 2021 compared to the first six months of 2020.¹
Hackers only need to get one employee to click on a malicious link, and your data and systems are exposed. Not only do you risk legal and financial repercussions as well as harm to your organization’s reputation, but cyberattacks have even recently caused human casualties. Gartner predicts that hackers will move to weaponize operational technology (OT) environments for this very purpose in the next few years.²
Your employees are the last line of defense in protecting against a cyber breach, yet many don’t have any idea how to recognize these threats.
Social engineering and phishing attacks
User access protocols
- Install malicious software
- Have the freedom to move laterally around your network
- Disable antivirus
- Encrypt data, and cause a ransomware event
Securing privileged access
In an IT environment, “privileged access” – also referred to as “God-like privileges” – is a term to select special access beyond a regular user. Privileged access can be related to human users as well as non-human users such as machine and applications identities. Protecting high-level administrative accounts is a critical component of a powerful security strategy against external threats, no matter the organization’s industry or size. Cybercriminals are looking for the big phish, and these accounts provide big gains for the bad guys.
As a best practice, privileged access should be reviewed to establish each user’s need. The accounts that remain should be closely watched to ensure proper use.
C-level exposure
Failure to report security issues
The longer a security issue goes unreported and not investigated, the larger the potential consequences. Employees need explicit instruction on how to report security incidents and suspicious behavior. They also need to know that they will not face ramifications for doing so.
Set up a hotline or email address where employees can report unusual behavior and security concerns. Promote the hotline by putting stickers on each employee’s and consultant’s laptop or hanging posters with hotline information and security messages.
READ: Why Security Incident Management Matters
Malicious acts
How to remedy human error in cybersecurity
Security infrastructure and software controls are only a portion of the solution to fend off cyberattacks in your organization. Your employees are the last line of defense against cybercriminals. Therefore, training employees about the role they play in cybersecurity is crucial to changing behavior and adopting a security-minded culture within your company. Security awareness training is never a one-and-done event; it is a constant journey with no destination, and it must be continuous in order to be effective.
Make sure your cybersecurity training addresses incident response and the responsibilities of all participants in every department and at all levels. Take learners through the process of dealing with a simulated attack scenario and provide them with hands-on training that will point out flaws in your response plan.
Cybersecurity awareness training from the experts
Is it finally time for your organization to get started with security awareness training or increase the effectiveness of your existing program? Global Learning Systems is a premier provider of security awareness, anti-phishing and compliance training for employees.
As a leader in behavior change for over 30 years, we tailor programs to meet each of our customer’s needs. Our engaging and memorable training content targets areas of vulnerability to create a security-minded and compliance-oriented workforce. Setting GLS apart is our understanding of human learning and the need for diversified training modalities to engage all learners and ensure retention. Our carefully customized training packages incorporate traditional courseware along with gamified training, microlearning, videos, assessments and more to guarantee successful knowledge transfer. Contact us today for a quote.
1. National Cybersecurity Alliance
2. Gartner



