The Open Web Application Security Project (OWASP) released its OWASP Top 10 2021 list of web application vulnerabilities in September 2021 during the celebration of the group’s 20th anniversary. The new list had been delayed multiple times. Scheduling the necessary collaborations to obtain data, performing the data science and analysis, and obtaining industry and media buy-in to drive awareness were all impacted by the COVID-19 pandemic. However, the new list was worth the wait.
Highlights of the New OWASP Top 10
With this latest Top 10, OWASP made several significant changes to its methodology in capturing and analyzing the data and ranking the vulnerabilities, including:
- No restrictions were placed on the CWEs (Common Weakness Enumerations) in relation to the data contributed. Previously, OWASP had provided a set of 30 CWEs in which there was interest, as well as a field to provide any additional findings outside of those CWEs. There was a realization that this actually hampered data collection, as contributors only sent data on the 30 CWEs identified. In this iteration, data was taken regardless of the impacted CWEs. This resulted in 400 CWEs being used to analyze the 2021 dataset.
- The increase in the number of CWEs required OWASP to make changes in how the Categories were structured. CWEs can be either “root cause” or “symptom” types. A decision was made to focus on root cause types, as these provide a better and more logical means of identifying and remediating vulnerabilities. It allows organizations to focus on the associated CWEs that impact the languages and frameworks they use. The number of CWEs associated with a Category in the 2021 list range from one (A10: Server-Side Request Forgery (SSRF), which is a symptom type CWE) to 40 (A04: Insecure Design, a new root cause Category).
- According to OWASP, “In 2017, we selected categories by incidence rate to determine likelihood, then ranked them by team discussion based on decades of experience for Exploitability, Detectability (also likelihood), and Technical Impact. For 2021, we want to use data for Exploitability and (Technical) Impact if possible.” This change in the methodology used to select the Categories resulted in some substantial changes in the rankings from 2017. Injection dropped from #1 to #3, its lowest ranking since the inception of the Top 10. Broken Authentication (now known as Identification and Authentication Failures) dropped from #2 to #7. Broken Access Control rose from #5 to #1.
- Eight of the 10 categories were selected from contributed data and two categories from the Top 10 community survey. The OWASP Top 10 vulnerabilities 2021 list is better balanced between data from previous breaches and current issues now being seen by application security and development experts “in the wild,” which are not yet reflected in the contributed data or the available automated testing functionalities.
- Each entry on the OWASP Top 10 2021 list now has an associated set of data factors, providing more transparency on the scope, rate, and impact of the vulnerability. They include:
- CWEs Mapped: The number of CWEs mapped to a category by the Top 10 team.
- Incidence Rate: Incidence rate is the percentage of applications vulnerable to that CWE from the population tested by that org for that year.
- Weighted Exploit: The Exploit sub-score from CVSSv2 (Common Vulnerability Scoring System version 2) and CVSSv3 scores assigned to CVEs (Common Vulnerabilities and Exposures) mapped to CWEs, normalized, and placed on a 10pt scale.
- Weighted Impact: The Impact sub-score from CVSSv2 and CVSSv3 scores assigned to CVEs mapped to CWEs, normalized, and placed on a 10pt scale.
- (Testing) Coverage: The percentage of applications tested by all organizations for a given CWE.
- Total Occurrences: Total number of applications found to have the CWEs mapped to a category.
- Total CVEs: Total number of CVEs in the NVD DB (National Vulnerability Database) that were mapped to the CWEs mapped to a category.
Comparing OWASP 2017 to OWASP 2021
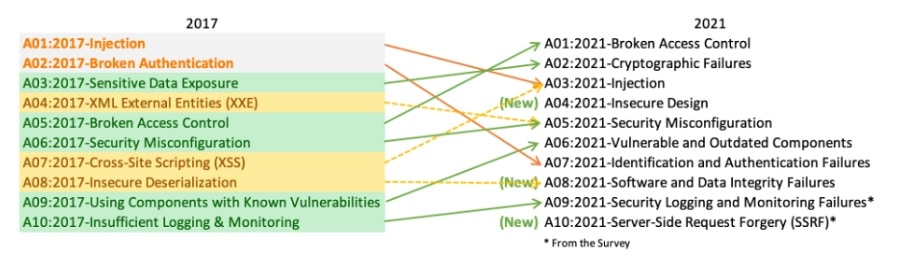
With the changes in how the OWASP Top 10 2021 list was compiled and ranked, what has changed from 2017 to 2021?
Three brand new entries were added:
- A04: Insecure Design, a new root cause-based category
- A08: Software and Data Integrity Failures, a new root cause-based category that includes Insecure Deserialization from the 2017 Top 10 list
- A10: Server-Side Request Forgeries, a new symptom-based category, which was #1 on the Top 10 Community Survey
Four naming and scoping changes occurred:
- A02: Cryptographic Failures (2017’s A03: Sensitive Data Exposure)
- A06: Vulnerable and Outdated Components (2017’s A09: Using Components with Known Vulnerabilities)
- A07: Identification and Authentication Failures (2017’s A02: Broken Authentication)
- A09: Security Logging and Monitoring Failures (2017’s A10: Insufficient Logging and Monitoring, which moves up three places due to its being #3 on the 2021 Top 10 Community Survey)
Four old categories were consolidated down to two:
- A03: Injection (now includes Cross-site Scripting (XSS))
- A05: Security Misconfiguration (now includes XML External Entities)
As you can see, the 2021 OWASP Top 10 is a momentous step forward in creating an awareness asset for development teams that better reflects what is happening in the industry.
GLS’s OWASP Top 10 2021 Secure Coding for Developers Course
The great news is that OWASP is now in better alignment with GLS’s approach to the creation of its secure coding course. GLS believes in the importance of root cause analysis of coding vulnerabilities, which is reflected in the structure of our category modules. We have looked past the 30 CWE approach since the beginning and have included prevention and mitigation strategies for vulnerability-related CWEs.
A great example of this is Injection. In prior OWASP iterations, Injection mainly focused on SQL Injection attacks. For our Injection module, we went broader and deeper, looking at nine different types of Injection attacks. The OWASP 2021 set of CWEs for Injections has expanded and covers a wider range of Injection attack types, an improvement we applaud.
GLS’s Secure Coding with OWASP Top 10 course is being updated to align with the new Top 10, including:
- Add new modules for the three new entries on the list.
- Add new modules to reflect the two sets of category consolidations while maintaining the four previous separate modules.
- Review and update previous modules to reflect changes in areas such as:
- Category title
- Category scope (e.g., move from a symptom to root cause)
- Impacts of emerging technologies
- Information on related data breaches that have occurred since 2017
Increasing developers’ awareness of their responsibility in relation to security will change how they program, which is the purpose of Secure Coding with OWASP Top 10 2021. Because GLS’s course is unique in its design, making changes to the course takes time to ensure we maintain its quality and effectiveness, including:
- The three new categories include two root cause types, requiring a longer lead time for research and asset creation for these modules that cover multiple vulnerabilities
- The two sets of consolidation require us to merge two full modules into one module while maintaining quality and not increasing seat time
Reviewing and updating existing modules requires time to modify and/or add content while not increasing seat time
We look forward to rolling out our updated secure coding course soon. Quality training takes time, and it is worth the wait.



