Imagine being in an emergency and suddenly your cell phone no longer works. Or perhaps you are in an accident, and you call 911 but cannot get through?
The services we rely on daily – cell phone service, financial services, energy, and utilities are becoming prime targets for cyberattacks. One ransomware attack can take down a financial system crippling access to your hard-earned dollars. A malicious click can cause a pipeline to shut down, leaving people without heat for days, weeks, or even months.
PAY-RANSOM OR CONSEQUENCE – YOUR CHOICE
The truth is that bad actors have found that targeting these systems with cyber attacks such as ransomware attacks create panic. Panic increases the likelihood that a target will pay to have the systems back up and running.
Cybercriminals are savvy enough to gain a foothold into a system, encrypt all the files, and then demand a ransom. Those who do not pay the ransom are taking a risk. Confidential data belonging to the company, employees, customers, and vendors could be leaked on the dark web.
THE CITY OF OAKLAND
The City of Oakland recently fell prey to a ransomware attack. The cybercriminal group, “Play,” infiltrated the City’s servers on February 8. They deployed custom-made software that enabled them to encrypt all of the City’s files. Then they demanded a ransom.
From what can be gathered from the limited response from city officials, the city refused to pay the ransom. This resulted in cybercriminals releasing information on the dark web. The information released included personally identifiable information of the employees including financial information, IDs, and passports. Other confidential information was released as well as data proving human rights violations.
It has taken eight weeks (8) to unearth what data is missing, who is affected, and how they are affected. During those eight weeks, critical systems came to a grinding halt. Ransomware is no joke.
EMPRESAS PUBLICAS DE MEDELLIN (EPM)
Empresas Publicas de Medellin (EPM) was targeted by cybercriminals with a BlackCat/ALPHV ransomware attack back in December of 2022. EPM is one of the largest public energy, water, and gas providers in Colombia.
EPM provides services to 123 municipalities and generated over $25 billion in revenue in 2022. EPM was forced to make 4,000 employees work from home due to the ransomware attack. IT infrastructure was down and the company websites were no longer available.
NEXTGEN HEALTHCARE
NextGen Healthcare was also hit with a BlackCat ransomware attack in January of this year. NextGen is an electronic health records vendor based in Atlanta with more than 2,500 healthcare organizations as customers. As of today, NextGen has not revealed information indicating that patient data was compromised.
BlackCat is known for its “triple extortion” approach. It combines ransomware attacks and threats to expose stolen data and disable websites. In contrast to other ransomware groups, BlackCat is notorious for posting compromised data on the open web versus the dark web. BlackCat also targets pharmaceutical companies and private clinics versus hospitals as many of its cohorts claim.
It has taken eight weeks (8) to unearth what data is missing, who is affected, and how they are affected. During those eight weeks, critical systems came to a grinding halt. Ransomware is no joke.
PREPARE YOUR ORGANIZATION
Many of these incidents, the City of Oakland especially, are believed to have happened because of insecure code. The insecure code then allowed bad actors right into the system. Unfortunately, this is something that happens all too often. Many cyber security experts believe these sorts of breaches can be minimized by implementing a zero-trust security model.
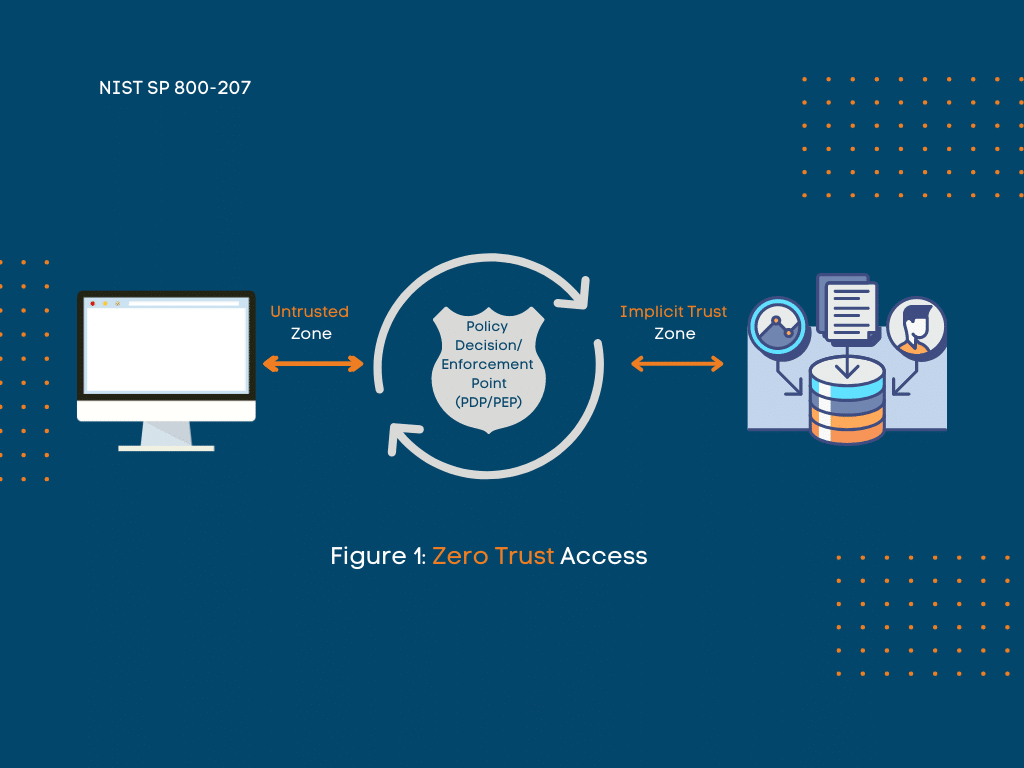
A zero-trust security model is a philosophy that denies access to IT systems. This applies to both internal and external people and devices. Access is only granted when necessary.
In other words, zero implicit trust. Organizations can better protect themselves against ransomware and other cyber-attacks by implementing a zero-trust security model.
This model restricts access to the system, making it more secure. However, this is a philosophy that too many city organizations fail to implement because of budget and time constraints.
TRAINING IS STILL IMPORTANT
Development and IT staff that are well-versed in secure coding are another prime assets. Training is an important part of your employee’s development. Training can be what makes or breaks your organization when it comes to data breaches.
One-and-done training, however, is not the answer. Organizations need an arsenal of weapons to fight threats. Role-based training, tailored training, and job-specific training are all crucial pieces of a cyber security training strategy.
Phishing though is still the number one tool used by bad actors to gain initial access to a system. Routine phish simulations and remedial training are key to an effective training program.
Never underestimate the power of a security-minded culture. When everyone is reaching for the same goal – a cyber secure organization – there isn’t much that can stop them.
Looking for something new and engaging to grab your users’ attention? Check out Global Learning Systems’s CSI:Phishing gamified training. CSI:Phishing puts your users in the “hot seat” as investigators challenged with finding the malware and source of the data breach. Click on the image below for a link to the game and see if you have what it takes to solve the puzzle.